
New year, new cybersecurity risks. As shown in our State of Cybercrime infographic, cybersecurity attacks specifically targeting workforce users are on the rise. We’ve witnessed this phenomenon throughout the past year as social engineering attacks targeted mainstream organizations, including a ride share app, a password manager platform, and a video game publisher. What’s the common denominator between these attacks? Workforce risk.
Workforce risk refers to the potential of each worker within an organization to trigger a security breach. According to Verizon’s 2022 Data Breach Investigations Report, 82% of breaches involve the human element. Now more than ever, having a dedicated program to manage workforce risk is necessary to improve an organization’s overall security posture—76% of cybersecurity leaders agree.
The right workforce risk mitigation technology and strategies will help lower the insider risk level of your business and, in turn, lower the potential of a security incident. In this article, we’re highlighting how Elevate Security helped drastically reduce human-related security issues for an S&P 100 enterprise with 40,000 users. Continue reading to get a glimpse into what you can expect to gain from implementing workforce risk mitigation tools.
The Problem with Workforce Risk
Not all employees are similarly risky and just a few employees cause the majority of security incidents. In fact, according to Elevate Research:
- 4% of employees/users trigger 82% of phishing incidents.
- 3% of employees/users trigger 92% of malware incidents.
- 2.5% of employees/users cause 50% of data handling incidents.
- 11% of users are the source of 71% of secure browsing issues.
All this to say, a small minority of workers trigger most security incidents.
Just like a small minority of drivers cause auto accidents. Why? They drive too fast. Get distracted. Forget the basic rules of the road. Make mistakes.
That’s why speed bumps work. They force drivers to slow down and pay attention. But folks hate them. They play havoc with suspensions, hubcaps, tires, let alone spilling hot coffee on the driver. Have you ever seen folks pull way over to the curb just to keep one set of tires off the speed bump?
What if there was a way to raise and lower speed bumps depending on the riskiness of each driver?
What if we knew that Bob was a careful driver who obeyed speed limits, didn’t use his phone while driving, and had passed a driver training review class with honors? If we could TRUST Bob to drive safely, we wouldn’t need to forcefully slow him down.
Mary, on the other hand, has 3 moving violations in 3 years. She frequently texts while driving, hasn’t been to a driver’s education class since high school, and she is 15 minutes late for the start of her shift at work. We probably shouldn’t trust Mary to drive safely, and it’s better for all of us if we put up the speed bumps to forcefully slow Mary down.
OK, a bit far-fetched, but the analogy holds true here.
We absolutely can know whether Bob or Mary is at high risk of creating a security incident. And, importantly, we absolutely can raise and lower the cyber speed bumps for each of them individually at machine speed. We can force Mary to use multi-factor authentication (MFA), while letting Bob use single sign on (SSO). We can limit where Mary browses, or what data she can access, or apply any number of security protections specific to her risk profile, all while maximizing Bob’s productivity and everyone else’s, too.
It really is that simple. Understanding individual risk factors and applying tailored protections to each individual:
- Dramatically lowers worker-instigated security incidents
- Protects individual workers in high-risk positions—engineers, developers, executives and others—from increasing sophisticated attacks aimed at their specific weaknesses
- Lowers internal cyber risk, making the organization and everyone in it safer
If you could (and you can) why wouldn’t you get your hands on this data and apply it?
Maybe you think it’s hard. It isn’t. We’ve built integrations with all the major sources of data that feed human risk analytics—many of whom are investors in Elevate.
Maybe you think workers will push back. Not true. We’re protecting almost a million workers today at some of the world’s largest organizations. Just like with their credit score, folks want to know where they stand on their own cyber risk. No one wants to be responsible for the next company-shuddering breach. Some of our customers have even tied compensation to good security hygiene. Those workers are very interested in knowing where they stand!
If this is resonating with you, let’s connect and discuss how Elevate can help you better know your people in order to strengthen your security.
Technology is the Solution
The best way to solve for workforce risk is by leveraging real-time data to develop behavioral scorecards that engage employees and motivate them on where they can do better, using social proof!
By leveraging data captured from various technologies (SIEM vendors, HR systems, IAM products, etc.) to track user actions and attackability, you’re empowered to measure and quantify unintentional insider risk in your organization.
With deep visibility into each individual’s user risk level, Elevate Security provides security teams with the visibility and risk scoring necessary to zero in on workforce risk, the most likely source of the next security incident, and stop it before it starts.
Let’s take a look at how Elevate Security’s workforce risk technology and data helped this S&P 100 enterprise reduce human-related security issues such as phishing, malware, and data handling.
➡️ To dig deeper into the use cases and benefits of behavioral scorecards, check out our blog, Human Risk Score: What Is It and How Does It Help Prevent Data Breaches?
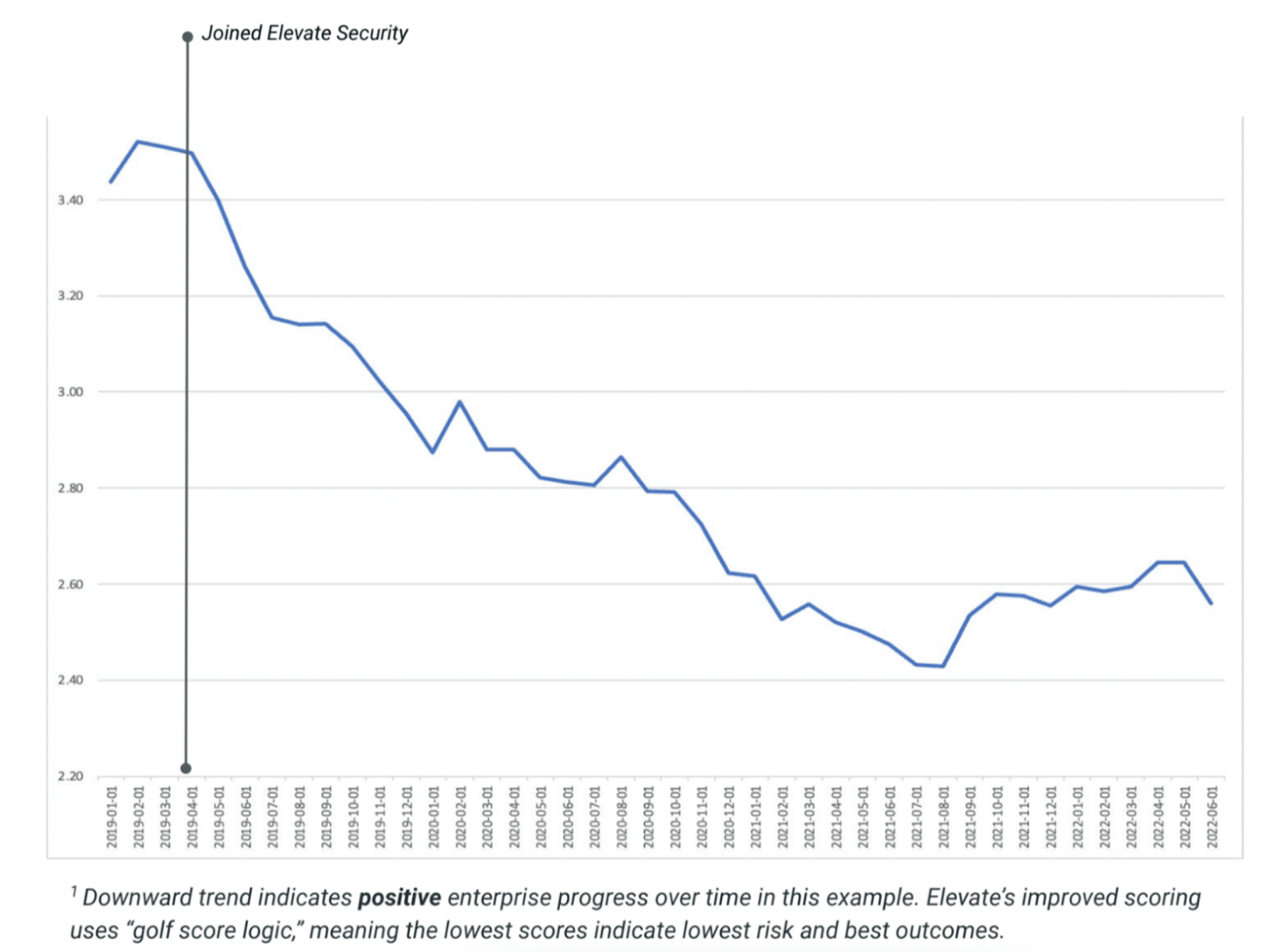
A Decrease in Phishing Attempts
Since implementing Elevate Security in April 2019, the enterprise customer below continues to experience an impressive downward trend in simulated phishing risk. As shown in the graph below, the enterprise’s risk score as it relates to phishing decreased from ~3.5 to ~2.5, leading to an approximate 28.57% improvement in individuals detecting and reporting phishing emails over time.
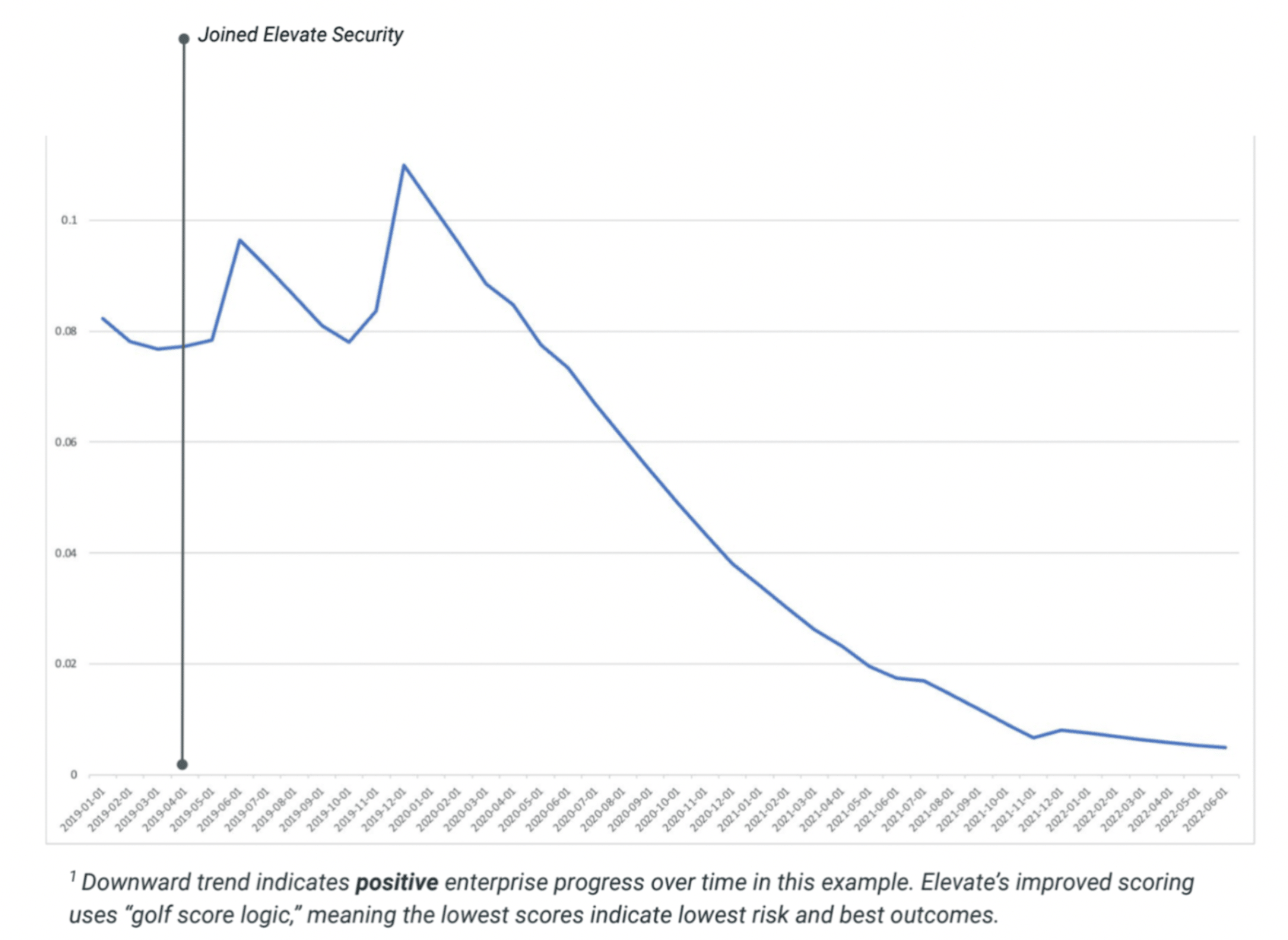
An Improvement in Malware Detection
From implementation in spring 2019 to June 2022, this S&P 100 enterprise also experienced a reduction in enterprise malware risk. With the help of Elevate Security’s workforce risk mitigation technology, this enterprise was able to improve individuals’ ability to detect malware, ceasing the download and/or execution of malware over time by approximately 77%.
A Rise in the Adherence of a Clean Desk Policy
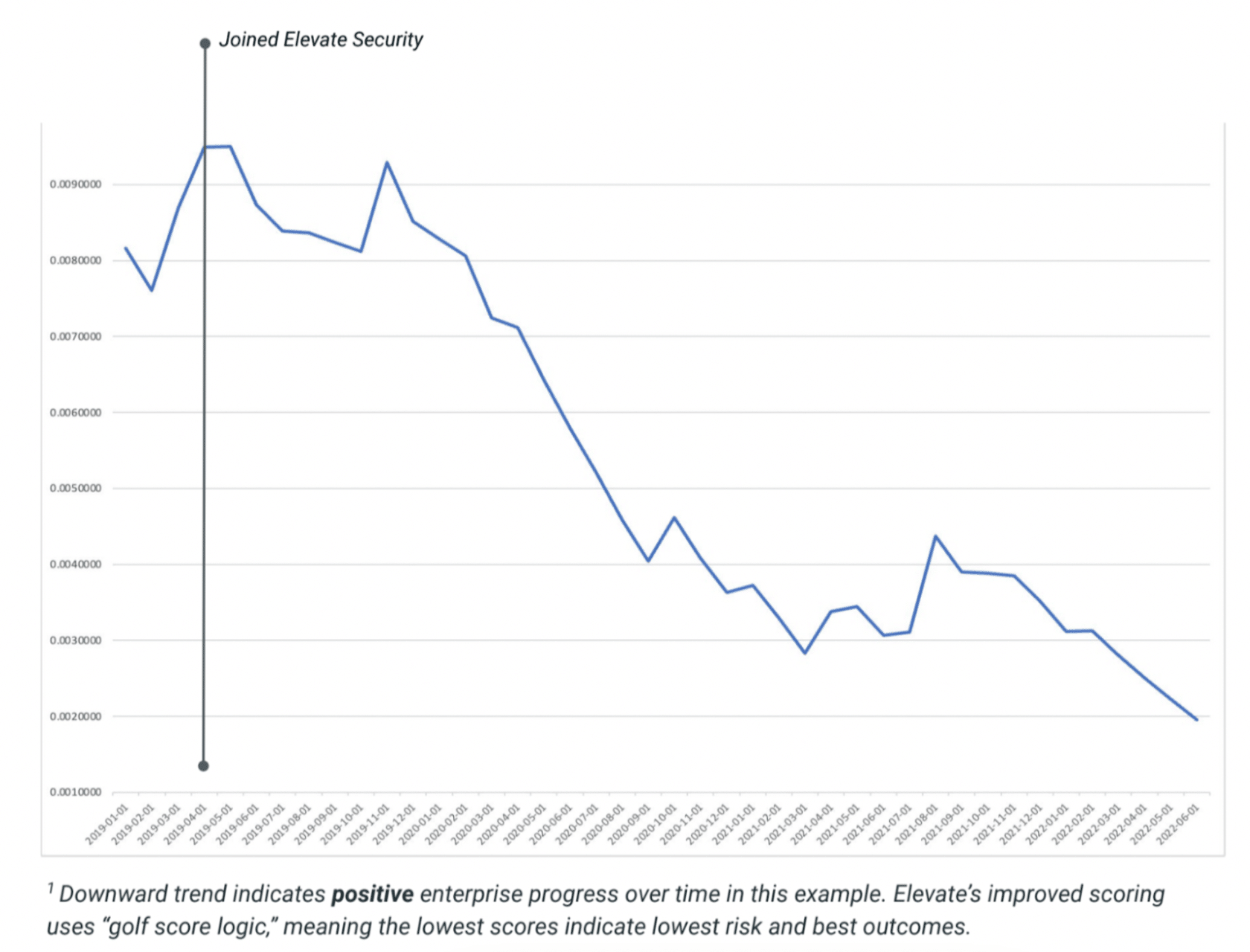
TechTarget defines a clean desk policy (CDP) as “a corporate directive that specifies how employees should leave their work space when they leave the office.” In today’s digital world, CDPs also require clean screens. In short, any sensitive paperwork, data or information left on a desk or computer screen that is left unprotected increases an enterprise’s workforce risk, potentially leading to unauthorized access, data loss, or theft.
Years ago, this S&P 100 enterprise instilled a CDP. Now empowered with Elevate Security’s data, the enterprise is experiencing a downward trend, indicating solid improvement over time in individuals adhering to the clean desk policy. The graph below shows the rapid decline from a risk rate over 0.1 to a rate well below 0.02.
Final Thoughts
The results are in—workforce risk mitigation technology is here. And just like speed bumps, it’s effective. What’s more, recent integrations with leading security vendors now enable the application of individual protections to match individual risk profiles. We can raise and lower cyber speed bumps depending on each individual’s risk.
A quick risk assessment will help you gain rapid insight into workforce risk and ongoing peer comparisons that help you track progress against industry benchmark goals.











