Today, identity management is top of mind for most security teams. That’s because a small number of employees (8.5%) are responsible for triggering 80% of security incidents. Cyber attackers are getting smarter too, with attacks growing ever more sophisticated day by day. They’re targeting new hires, folks who’ve changed roles, and individuals with access to the most sensitive data. That being said, there has been a 2.5x increase in attacks against engineers who have direct access to an organization’s source code. Not to mention:
- 84% of organizations experienced an identity related security breach during 2021-2022
- 80% of cyberattacks utilized identity-based techniques to compromise login credentials and deceive security teams
- 96% of companies believe one of their recent breaches was preventable with identity-related security measures
So what are today’s identity management programs missing out on? The injection of user risk into authentication and authorization processes. Elevate Identity solves this problem by helping organizations:
- Inject user risk data into identity systems to automate conditional access policies, revoke access based on verified threat signals, and enhance access governance reviews
- Ingest and aggregate data from the enterprise to identify and score individual risk based on behaviors and attack history
An Insider’s Look into Elevate Identity
By adding user risk into authentication and authorization processes with Elevate Identity, security teams can frustrate adversaries attempting to gain unauthorized access. The result? A lesser likelihood of an adversary successfully establishing persistence and performing lateral movement. This leads to reduced incidents of unauthorized access and helps avoid post-incident cleanup.
Let’s take a closer look at how Elevate Identity works to improve identity management and how to navigate the platform.
The Elevate Dashboard
In the Elevate Identity dashboard, you can easily see the riskiest individuals, departments and locations as well as the factors taken into account to determine that risk—all in one place.
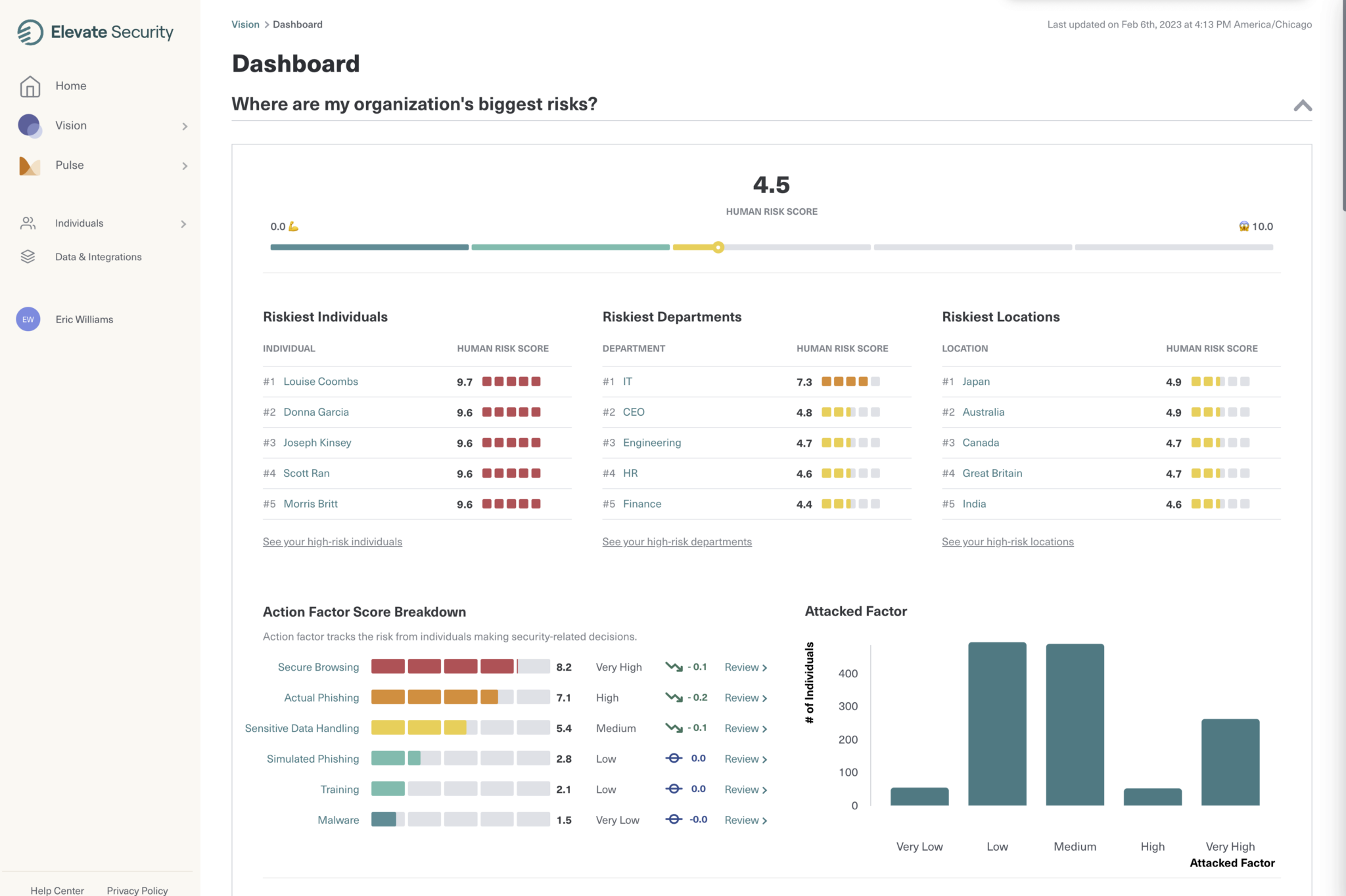
Where do these insights derive from? Context and insights are built through API integrations with core security technologies such as email security, endpoint, web gateways, and other tools, to generate high confidence risk signals based on user behavior and patterns of attacks.
Now, let’s dive in on how you can make smarter identity management decisions using the behavioral and attack data pulled in to elevate.
Individual Reporting & Risk Management
Let’s look at an employee’s risk profile. Take Walter, for example. He’s a member of the engineering team and his risk profile shows that he’s particularly risky across multiple behaviors as he:
- Recently downloaded malware
- Browsed to sites he shouldn’t
- Clicked on phishing links
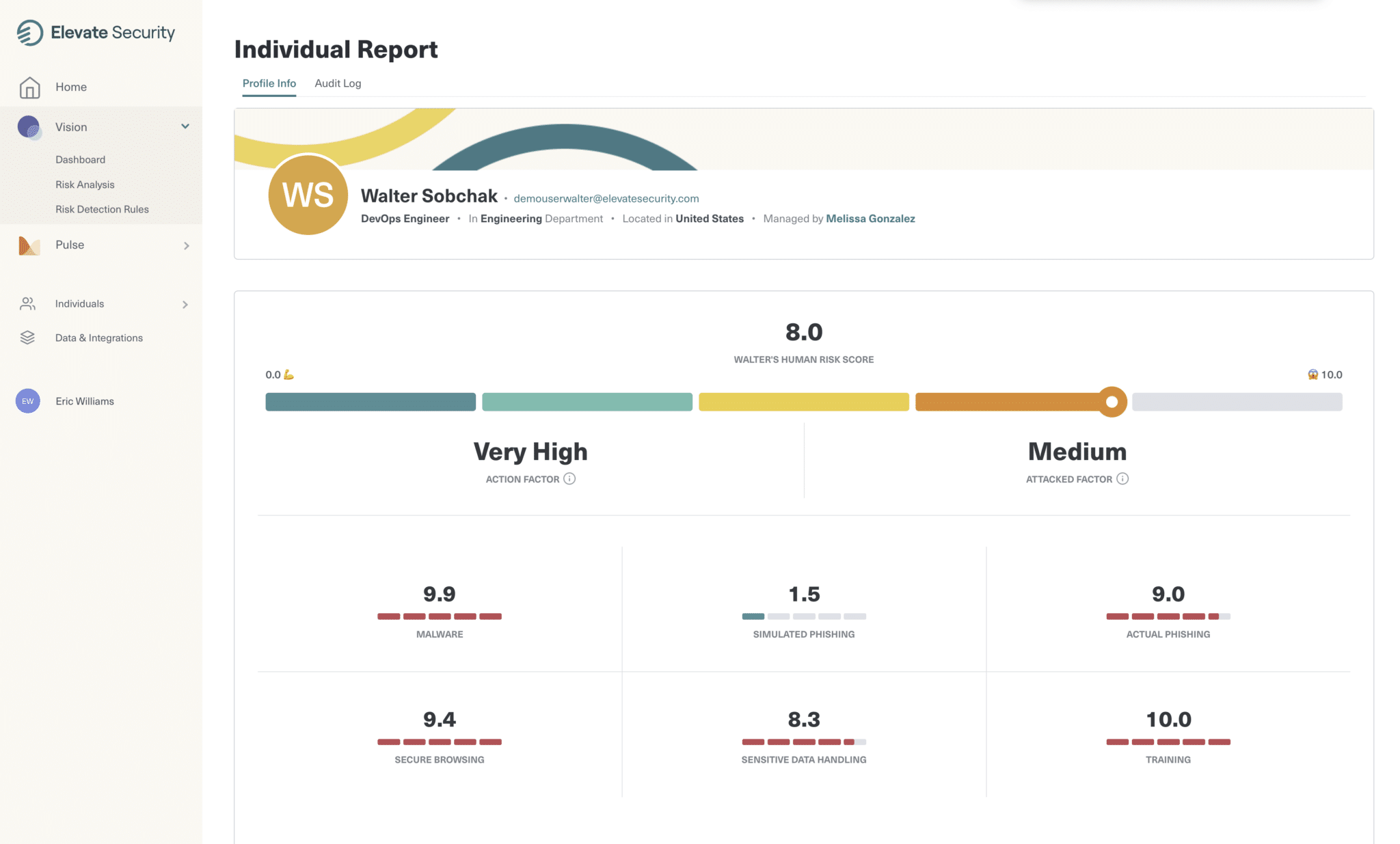
If he were your employee, you’d still want to enable him to do his job, but you’d also want to ensure that you put the right response in place to safeguard his identity and access. You can do this by using conditional access policies.
Automated Conditional Access Policies & Access Review Process
Let’s keep moving forward with Walter as our example. Through his Individual Report, it’s evident that because he’s an engineer and his overall risk is high, Walter has been added to a high-risk engineer group automatically. He’s additionally been added to this group because he’s exceeded the risk threshold.
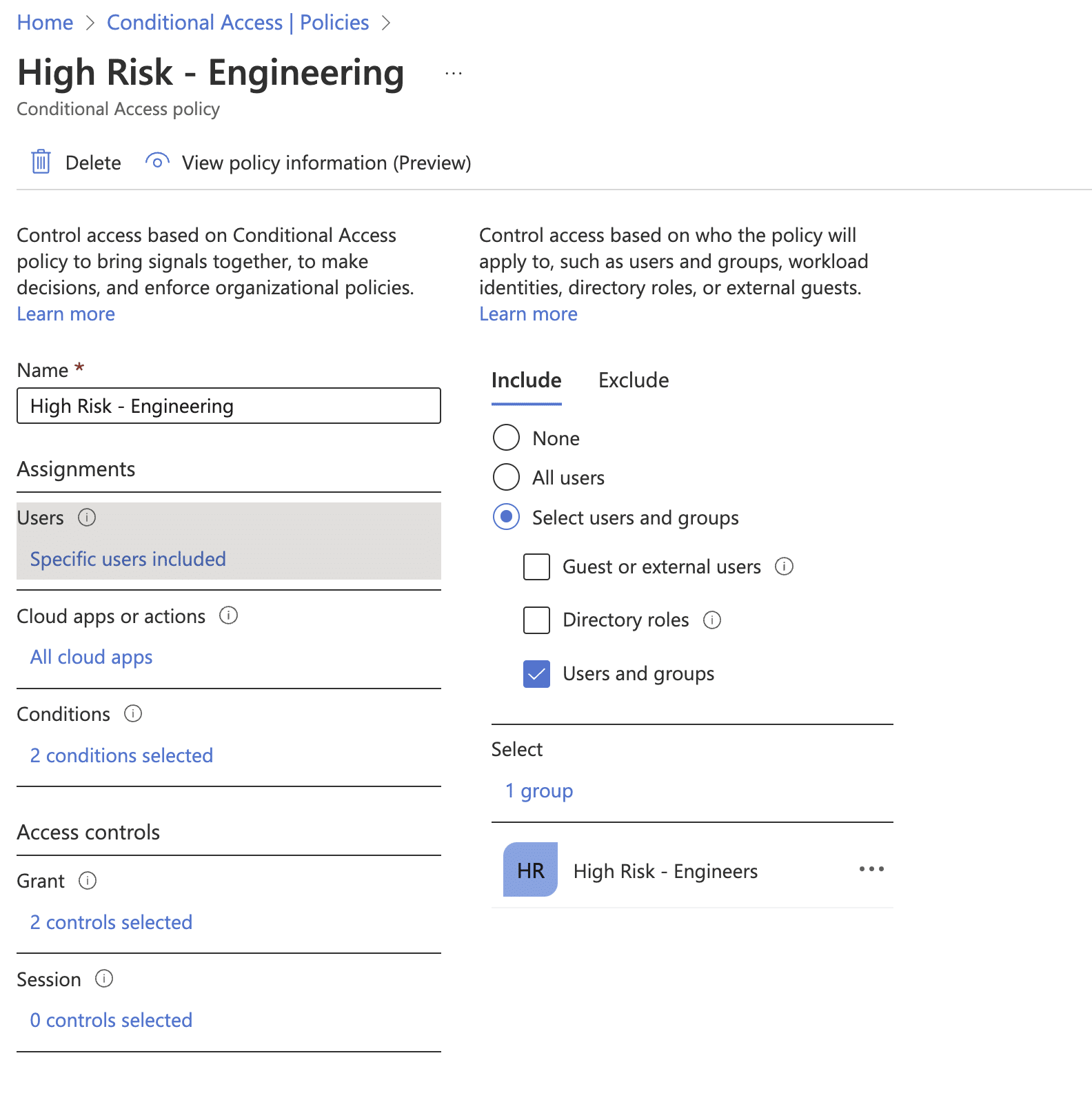
Looking at the conditional access policy he’s been assigned, you can quickly see that the next time he authenticates, new requirements will be set:
- First, multi-factor authentication will be mandatory for him across all accounts
- Second, he’ll need to login to the system through a trusted location
- Third, he’ll need to use a company compliant device that meets the company’s security policies
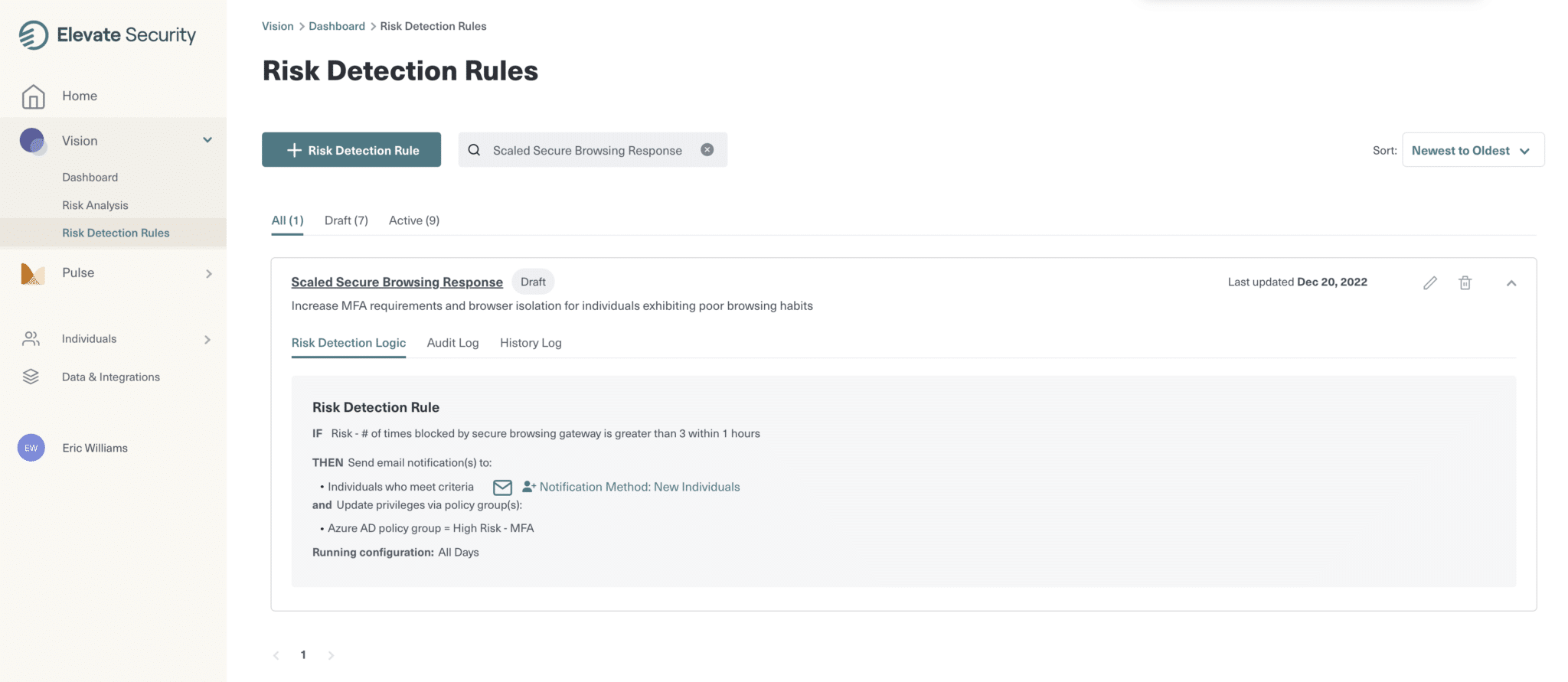
Now you can sleep better at night knowing that you’re not inadvertently giving access to an adversary because of Walters’ bad decisions.
Additionally, once Walter was placed into a high-risk engineer group, his access review process changed. No longer does it happen once a year where a manager rubber stamps the approval—it now happens quarterly. The review will include the risk details in the approval process and add an additional sign off from the security team.
This type of access review process helps ensure your riskiest individuals have the least privilege yet are still enabled to tackle their workload with little friction.
See Elevate Identity in Action: Watch the Demo
Elevate Identity helps you better protect employees like Walter while keeping productivity high throughout the organization. With Elevate, high-risk users receive more strict protections that would be impractical for the entire user population. Meanwhile, low-risk users could benefit from policies balancing productivity and satisfaction.
The security team achieves a best-practice approach to identity management, resulting in reduced incident rates, lower organization-wide risk, and fewer issues requiring triage and response.
Watch the brief demo of Elevate Identity and learn how it can help you make smarter access decisions by enforcing conditional access policies and reviews based on verified user risk behaviors:
Final Thoughts
You can’t afford to allow adversaries into your networks and systems. But without the right tools to better safeguard your high-risk employees from triggering a security breach, the chance of an adversary infiltrating your organization increases.
By integrating Elevate’s broad-spectrum user risk intelligence into the identity management framework, security teams can proactively authenticate the risk of the user attempting to access their systems. We hope this demo gave you deeper insight into the use cases and benefits of Elevate Identity. If you have further questions, we’d love to chat through them with you—get in touch with us.











