Elevate Identity
Identify Human Risk & Strengthen Access to Critical Resources
Research finds that 8% of employees contribute to 80% of an organization’s security incidents. Let’s solve for this!
The Problem — Human Risk Isn’t Equal
'One-size-fits-all' protections to sensitive resources or transaction approvals don’t account for risk disparities between good cyber employees and users engaged in high-risk, potentially compromised behaviors.
The Solution — Conditional Access
Elevate Identity provides user authentication workflows with human risk intelligence as a control factor for approving, denying—or—initiating conditional requirements for access to business critical resources.
Latest News
Elevate and Cyentia Institute Earn "Top-Rated Session" status at RSA 2023
@Work: Human Risk Intelligence as a Condition of Access
Dive Deeper
Learn more about Elevate Identity
Learn more about Dynamic Risk Response
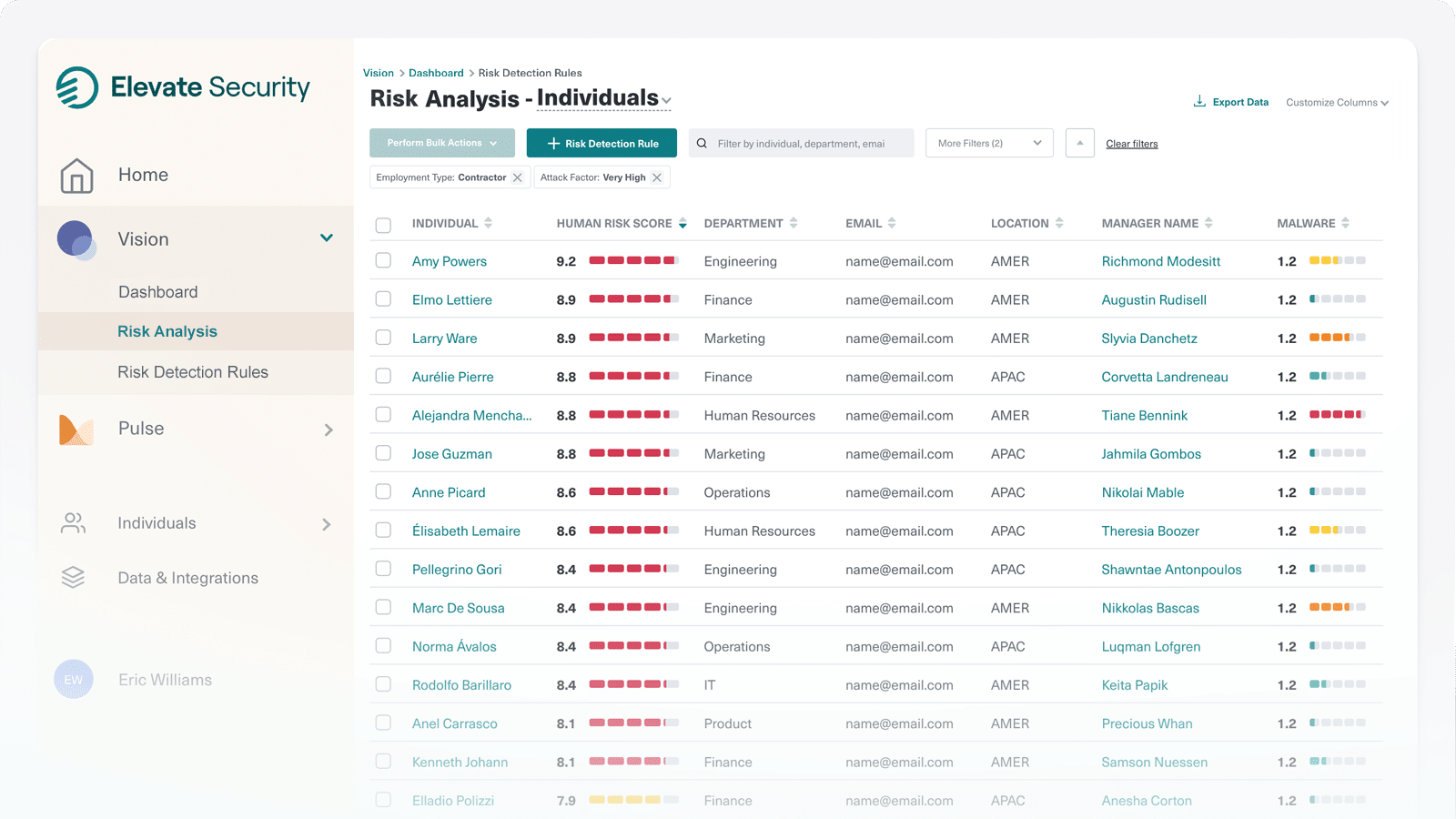
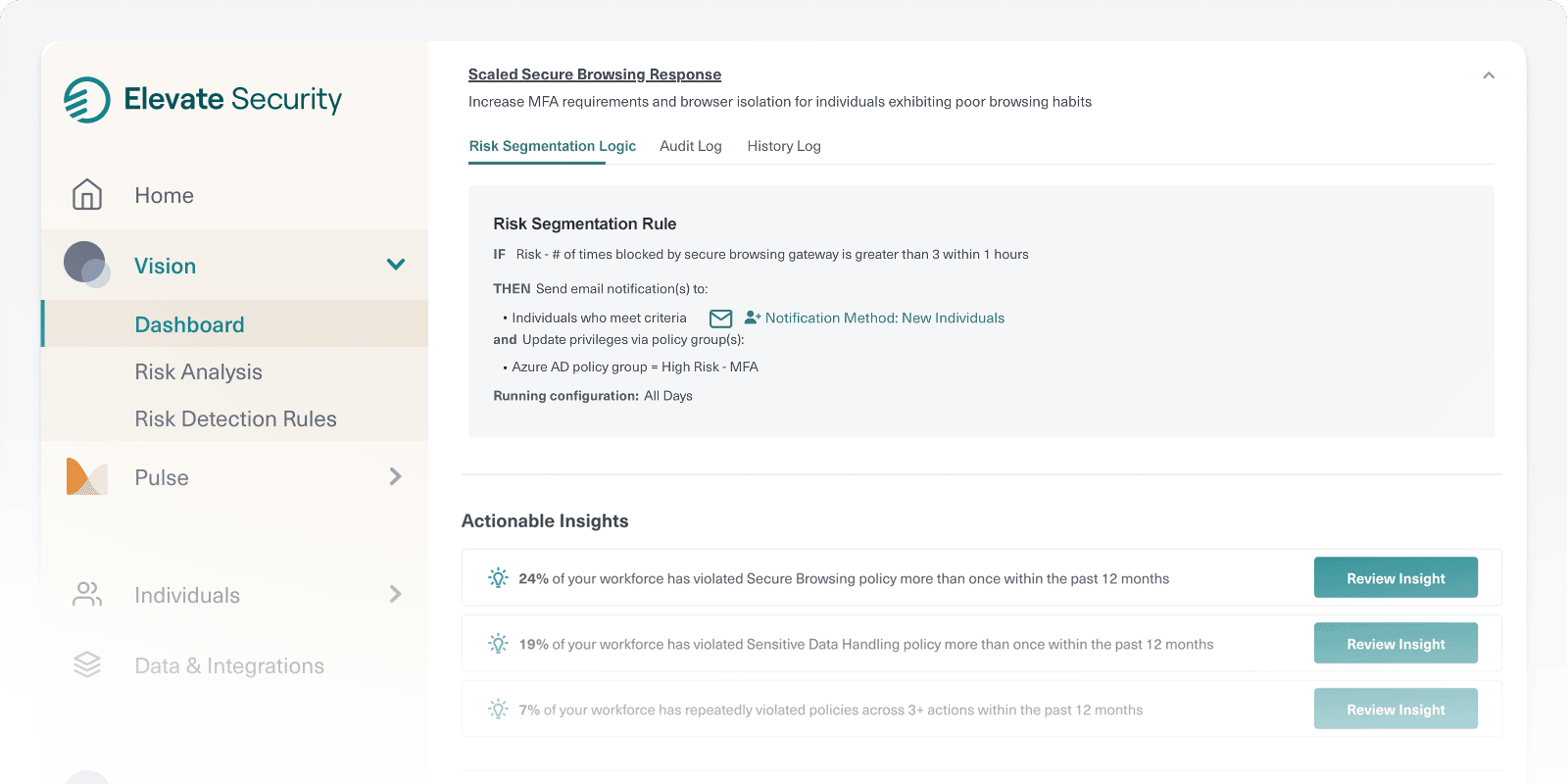
How Elevate Identity Works
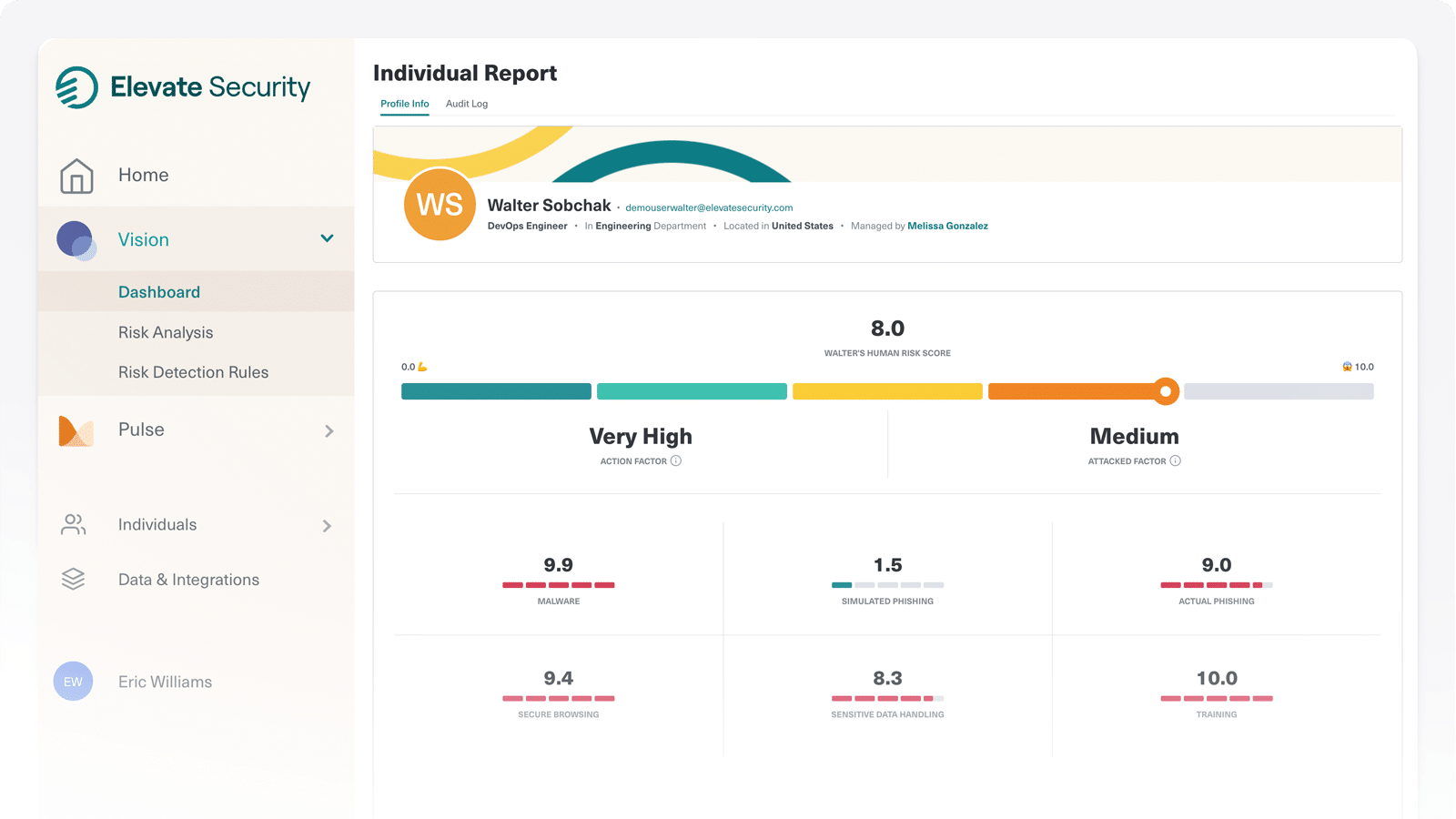
Elevate ingests and analyzes data from across your enterprise to identify and score individual risk based on behaviors and attack history.
Now, in addition to an organization’s use of strong authentication requirements such as something an employee has (token) or something they are (fingerprint), you can apply ‘something they are doing’ (threat signals) as context for access decisions.
Review a Personal Demo with an Elevate Expert
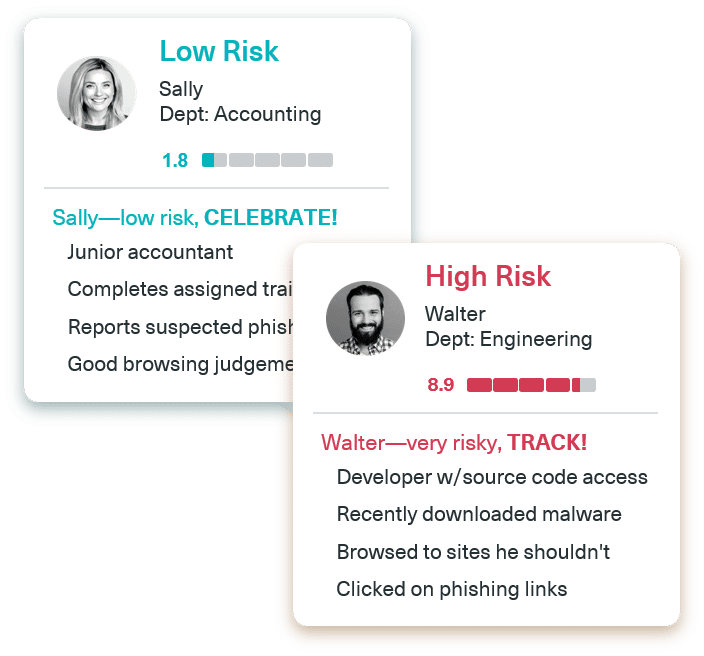
Strengthen Defense for High-Risk Users
Request an Elevate Security Demo Today
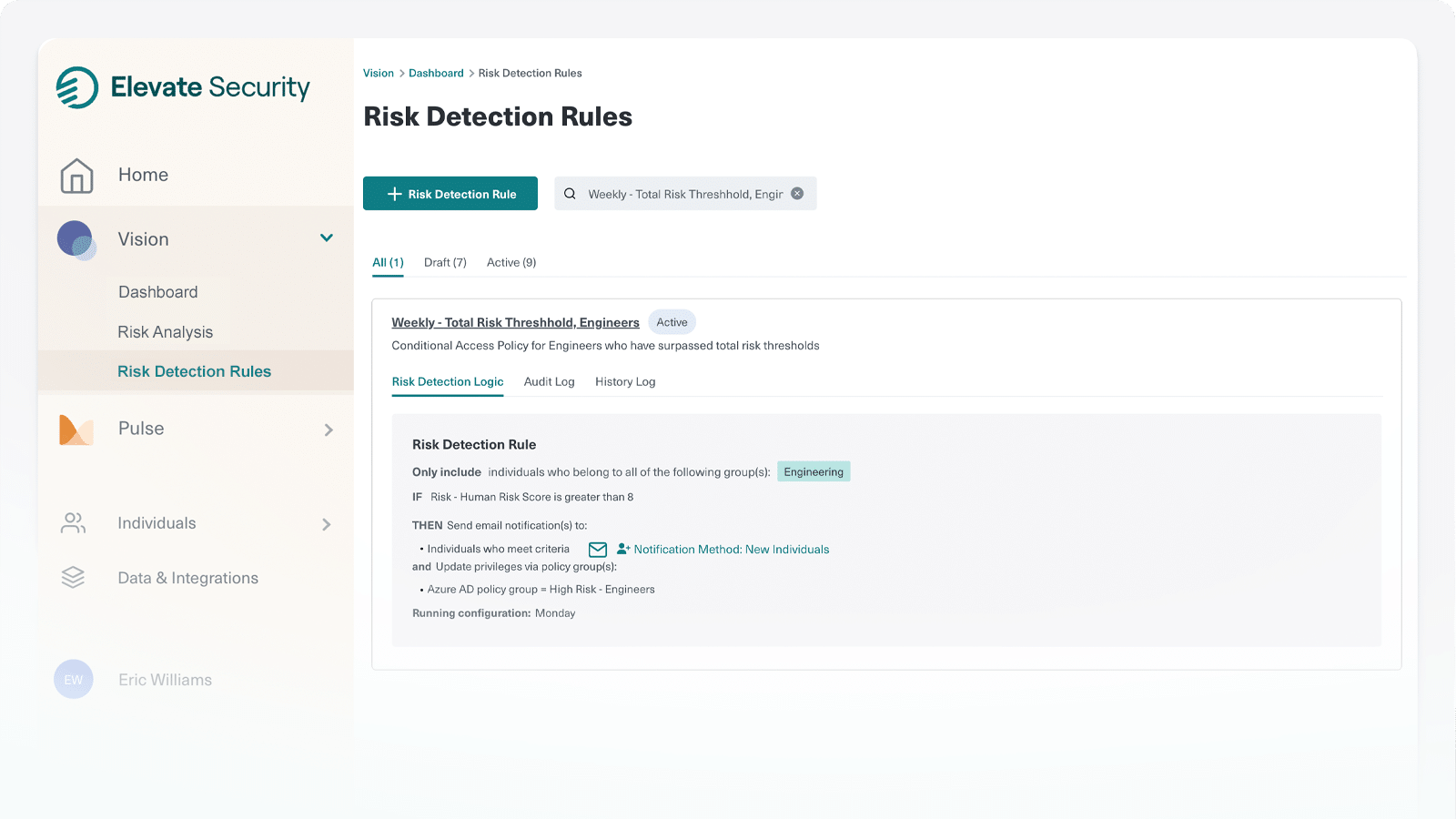
Dynamic Risk Response for Smarter IAM
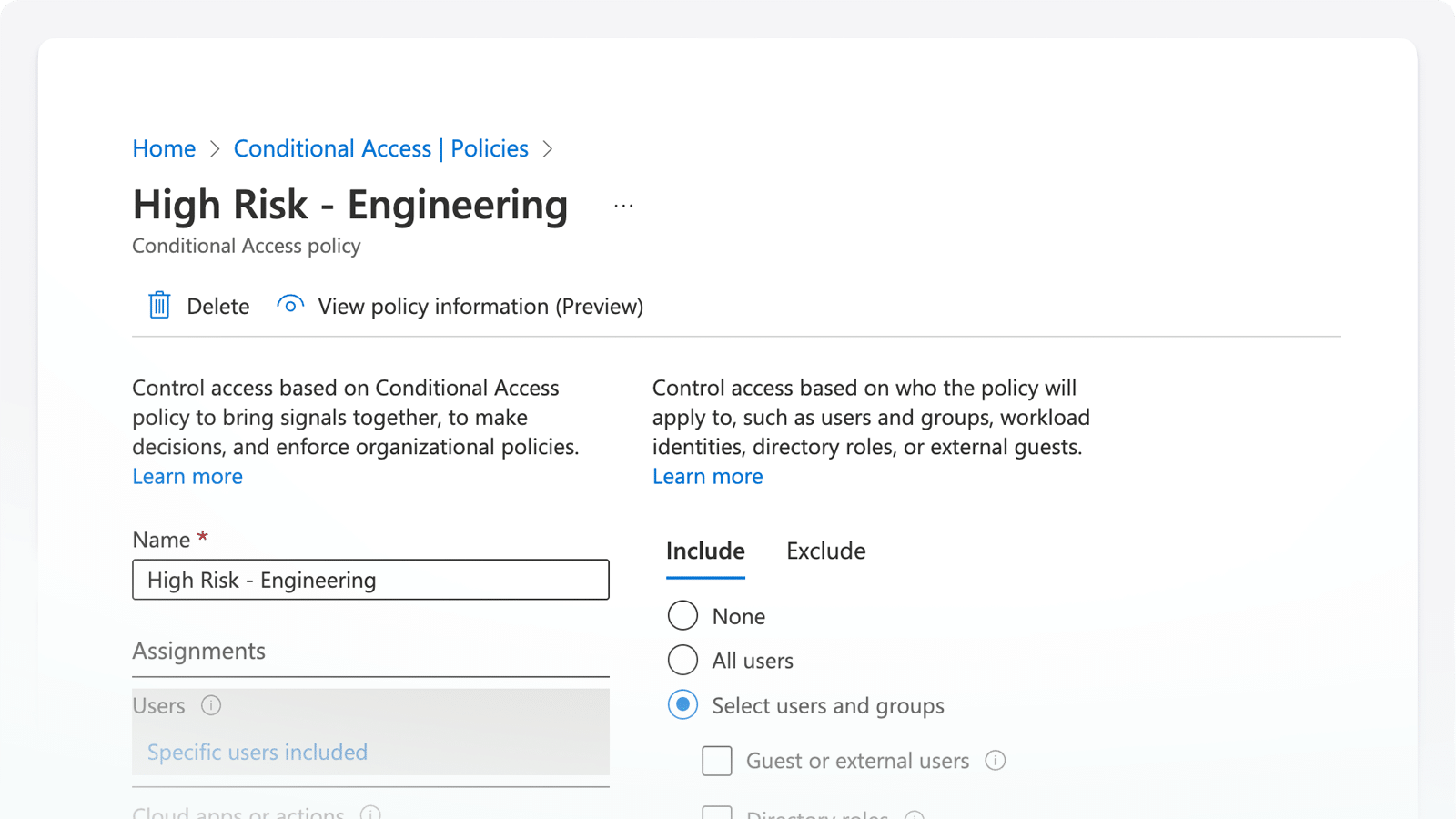
Automate Conditional Access
Enforce conditional access such as enhanced MFA, device restrictions, or trusted location requirements based on dynamic mapping of user actions and risk thresholds.
Act on Risky Behaviors
Automatically revoke active sessions and remove access to resources based on threat signals and actions that indicate potential account compromise.
Intelligent Access Reviews
Insert human risk intelligence into access governance workflows to ensure the right level of approval scrutiny is available to decision-makers.
Strengthen Identity Management for High-Risk Users
By applying human risk as a factor in securing access, you’ll gain a new and powerful control for defense against the unpredictability of risky and often hidden user behaviors that create unintentional security gaps.