Solution Sheet

Strengthen Identity Governance with Human Risk Intelligence
Enhance defense of user access to critical business assets by providing human risk intelligence as a contextual factor when provisioning and reviewing employee access to enterprise resources.

Addressing Today’s Biggest Cybersecurity Gap, ‘Employee Risk’
When you know who is risky and why, you have a tractable problem that’s solvable. Let’s dig deeper!
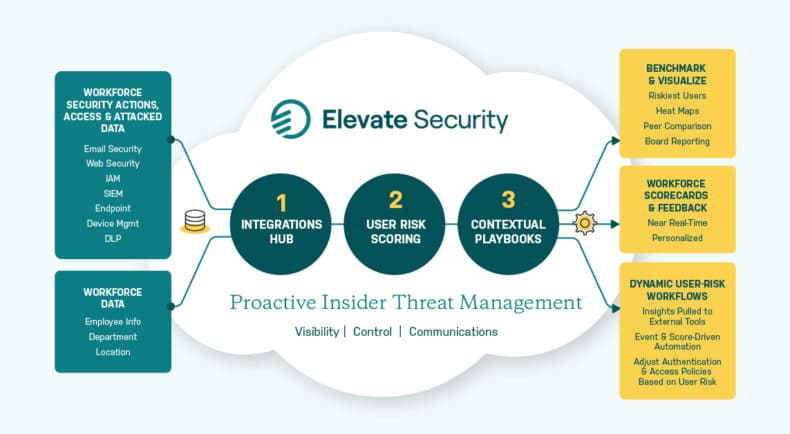
Elevate Security Solution Overview
Elevate Security bridges the gap between firefighting incidents and proactively protecting your workforce against ransomware, data loss, and account takeover. This Solution Overview explains how customers take action on predictive risk with benchmarking , real-time feedback & notifications, workflow automation, and tailored security controls.

Account Compromise Industry Solution Brief: Biotechnology
Elevate Security Platform prevents account compromise in Biotechnology by empowering enterprise security teams to break the attack kill chain. This solution sheet details how we stop Biotech IP loss caused by account compromise. Proactively protect your end users who are most likely to have their accounts compromised.

Account Compromise Industry Solution Brief: Financial Services
Elevate Security Platform prevents account compromise in Financial Services by empowering enterprise security teams to break the attack kill chain. This solution sheet details how we stop the financial data loss caused by account compromise. Proactively protect your end users who are most likely to have their accounts compromised.

Account Compromise Industry Solution Brief: Technology
Elevate Security Platform disrupts the attacker’s tactics along the account compromise kill chain threatening your DevOps lifecycle. This solution sheet details how we proactively defend DevOps using an end user Zero Trust approach. Know which developers are most likely to be compromised.

Elevate Security for Account Compromise
Elevate Security Platform helps your organization defend itself against account compromise. This solution sheet details how we disrupt the likelihood of account compromise success, manage all necessary controls automatically, and actively manage your account compromise posture over time. Understand which users are at greatest risk of falling for an account compromise attack.
Try a Demo Today
We'd love to show you how it works. To see a personalized overview of the product, you can schedule a demo.






