Internal users’ unintentional mistakes represent over 85 percent of security events.1 But who are these users? How many of them are running rampant at your organization? What risky behaviors do they exhibit? Finding the answers to these questions is no easy task.
Cyentia’s new report, The Size and Shape of Workforce Risk, offers us some keen insights.
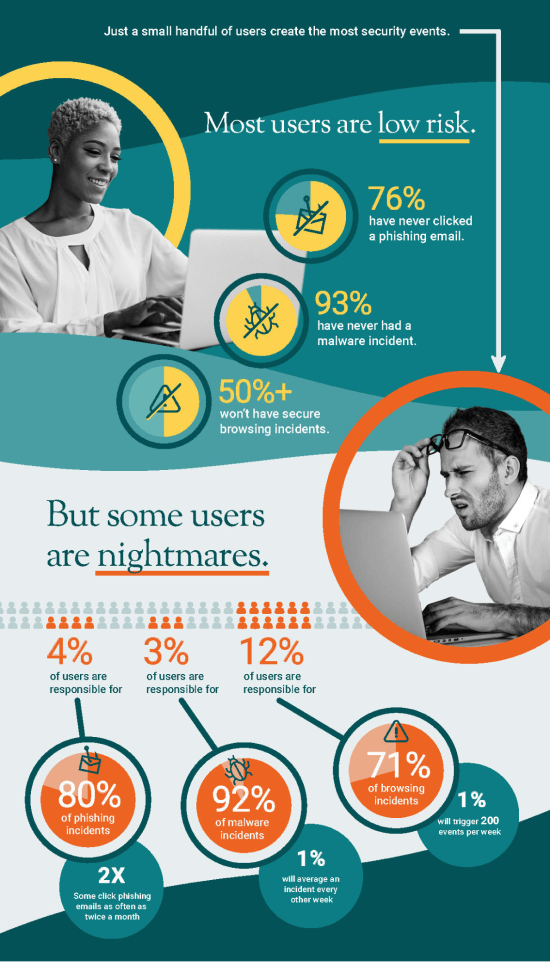
It turns out most users are low risk, with 76% never clicking a phishing email. While 4% of users are responsible for 80% of phishing incidents. On top of that, your high-risk users are more likely to be repeat offenders and prone to introduce risk in multiple areas. The challenge is proactively identifying them.
One Size Does Not Fit All
Applying the same security controls across your organization won’t significantly impact your risk profile. Your highest risk users represent a small percentage of your workforce and exhibit multiple, overlapping risky behaviors. Focusing on those users with targeted security controls and communications is a far more effective strategy.
Pinpointing high-risk users, building individual reputation scores, and adjusting your security policies accordingly will allow you to proactively protect your organization from attack. But the first step is finding them.
The Size and Shape of Workforce Risk: A Cyentia Study
Stop indiscriminately applying security controls across the board. Learn how to identify your riskiest users and take the first steps to answering the following questions:
- Are there a lot of risky users or just a few?
- What exactly do we mean by “risky” anyway?
- Are some users more prone to risk than others?
- How can we help them engage in less risky behavior?
- What kind of impact on our incidents could proactively identifying our risky users have?
The Cyentia Study, in partnership with Elevate Security, will help you to start making sense of the user risk landscape in your organization and begin measuring your true risk profile.
Elevate Security identifies and responds proactively to an organization’s riskiest users, providing security teams with the visibility and playbooks necessary to prevent the next security breach.
___________
1 Verizon 2021 DBIR