Smarter Identity Access Management
User-Risk Aware IAM
Your Problem
Today, you don’t know the user risk behind an attempt to access your systems. Basic Identity data – user credentials, location, network, and device – doesn’t offer insight into the risk profile of the person behind the access attempt.
Without visibility into user risk at the time of authentication and authorization, your chances of letting an adversary in and allowing them to achieve persistence increases. Dramatically.
Our Solution
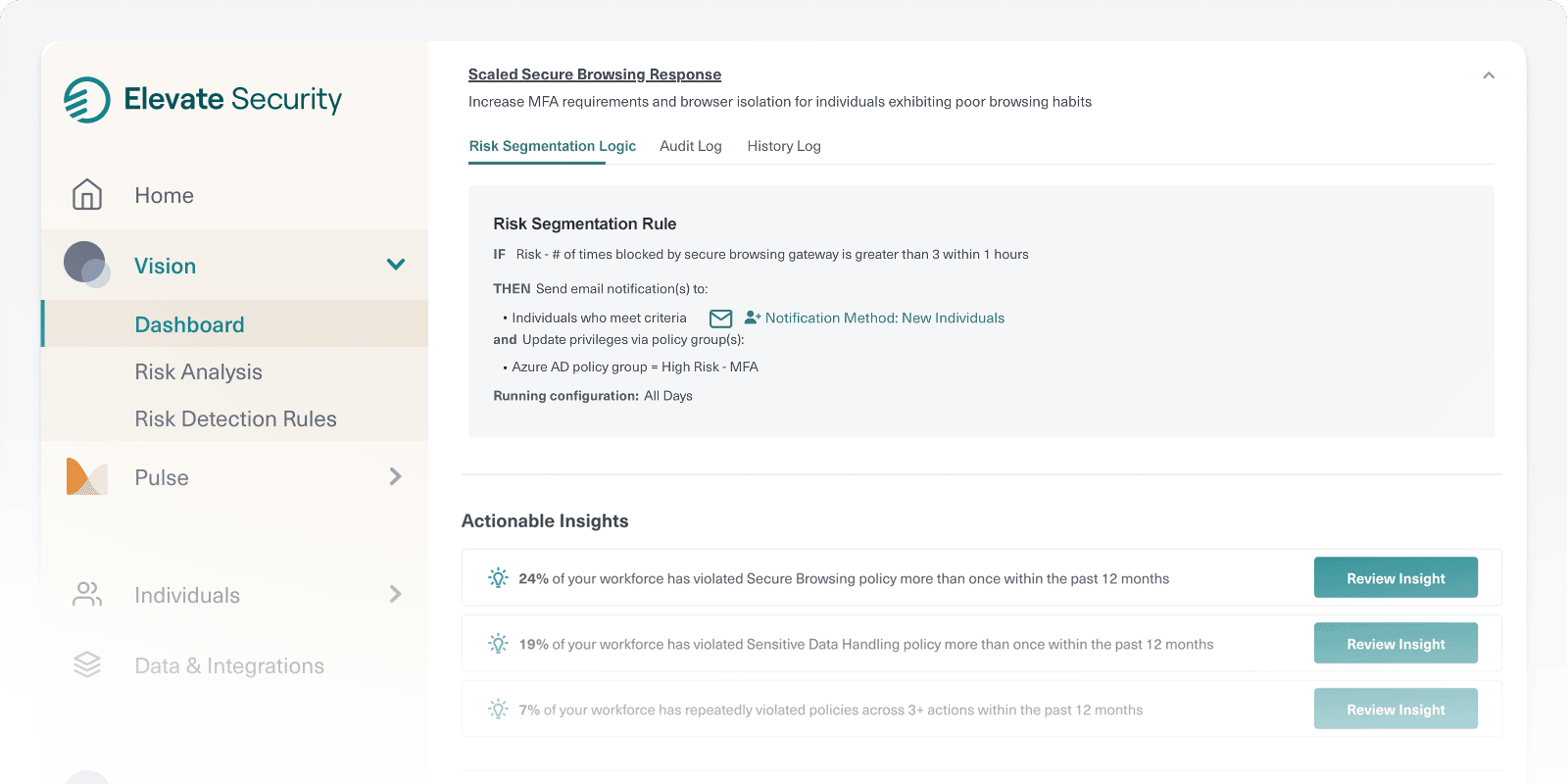
Elevate adds comprehensive user risk information that enriches traditional Identity data, providing a 360° profile of the human behind each access attempt.
By infusing Identity and Access Management (IAM) with Elevate data, security teams gain a unique element of human risk scoring during the authentication process, leading to stronger defense against unauthorized access, and the costly consequences of a cyber incident.
Introducing Elevate Identity
Download the Solution Brief
Download our solution brief to learn more about Identity Access Management
Identity Access Management Made Smarter with Elevate
Elevate works with Identity and Access Management systems to increase the effectiveness of your Conditional Access strategies. Elevate gathers context from across your estate, including email security, Endpoint Detection and Response (EDR), web gateways, Security Information and Event Management (SIEM) solutions, and other technologies, to generate a high-confidence risk signal for each user based on their past system usage decisions, current behavior, and any attacks already targeting them
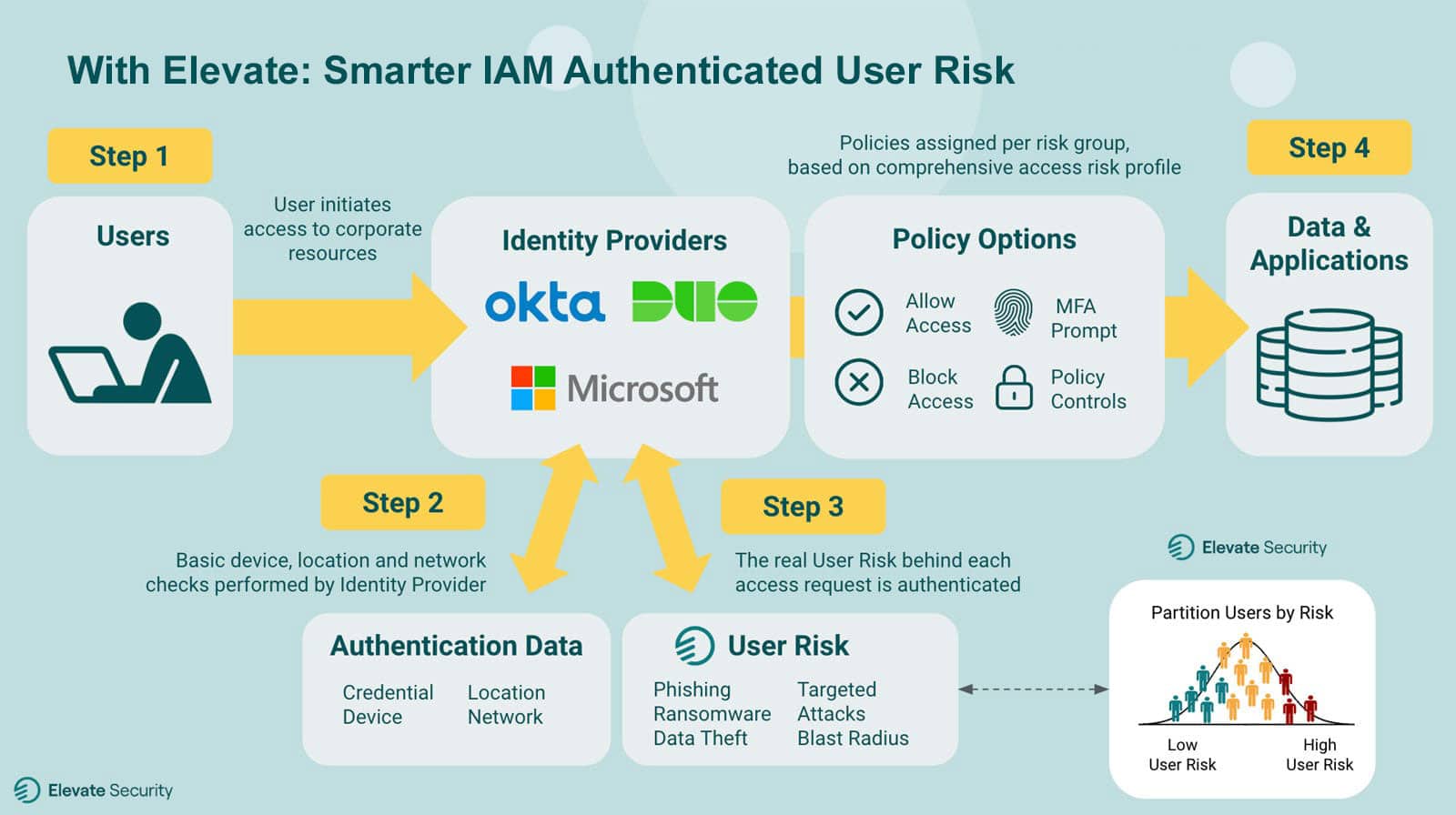
Step 1
User initiates a request to access corporate applications and data.
Step 2
Identity provider runs basic checks on credentials, device, location, and network.
Step 3
Elevate verifies the true human risk of the user behind the request.
Step 4
Better informed and smarter policy decisions are made during the user authentication process.
By partitioning user risk during authentication and authorization, security teams frustrate adversaries attempting to gain unauthorized access, with less likelihood of an adversary successfully establishing persistence and performing lateral movement. Also, because Elevate integrates directly into core security automation and triage tools (SIEM, Security Orchestration, Automation and Response (SOAR), and Case Management) security teams can prioritize, triage, and drive additional security workflows based on user risk.