
When it comes to incident detection and response, the cybersecurity solution landscape is very crowded and often can be confusing. When CISOs and security teams think about their needs and the problems they are solving, there are several frameworks that can be applied.
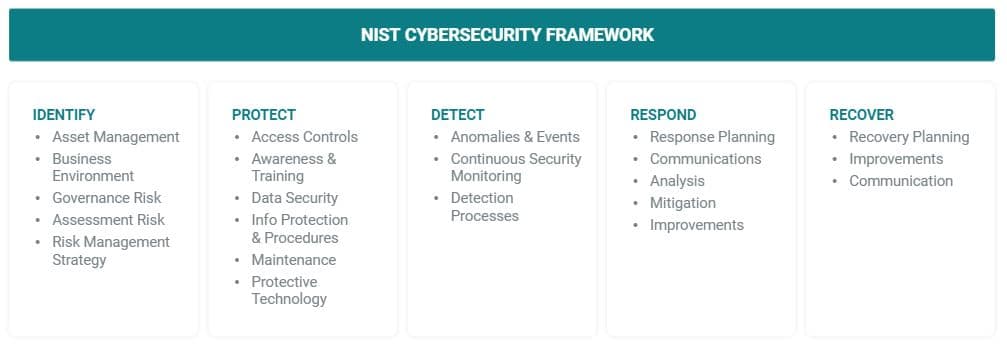
By far, the most popular is the NIST Cybersecurity Framework, which orients the cybersecurity market into 5 primary buckets: Identify, Protect, Detect, Respond and Recover.
Because timely incident detection and response is so critical, the marketplace is flooded with all manner of monitoring tools, alert correlation, and remediation solutions. The past decade has witnessed an alphabet soup of acronyms emerge that aim to address incidents at a deeper level, however. These include:
- Security Information & Event Management (SIEM) – solutions that correlate and normalize security log data to detect incidents, send alerts, and manage incidents. c.2005
- User & Entity Behavior Analytics (UEBA) – solutions that examine patterns of system and/or user behavior to detect anomalies that may indicate potential threats. c.2014
- Security Orchestration, Automation & Response (SOAR) – solutions that automate incident response across security tools using playbooks that eliminate manual work. c.2015
These solutions have built on each other, in a natural evolution born of product feedback in the following progression, plainly stated:
- I want to search my data for bad stuff.
- I want to automate finding the bad stuff.
- I want to automate the cleanup of bad stuff after I find it.
Simple enough, right? The problem with only focusing on incident response is that, after you recover from a breach, it’s never over.
Closing the Gap Left by SIEM, UEBA and SOAR
In actuality, the NIST Framework is a continuous loop. After any attack, a closed loop should provide feedback to “identify” and “protect” better, next time. Yet most SIEM, UEBA and SOAR products stop at “recover”.
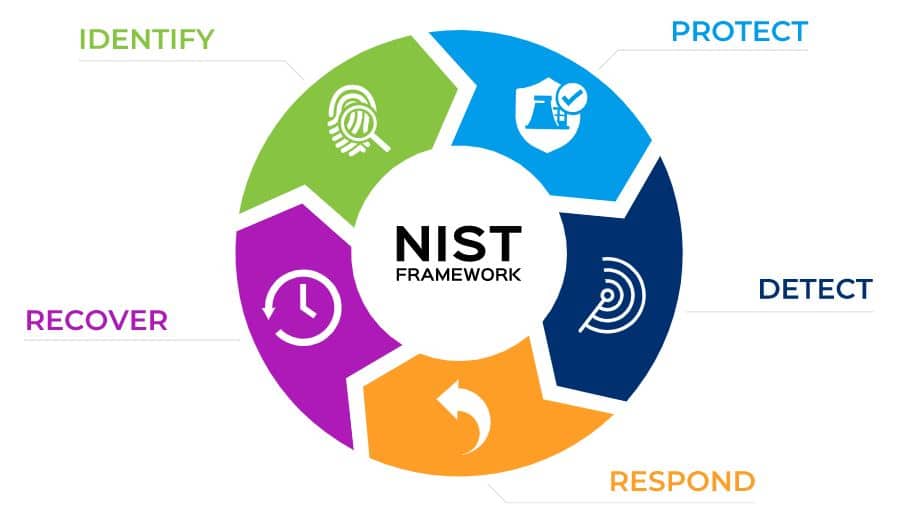
So if your organization employs a SIEM, UEBA or SOAR, there’s a big gap in your solution.
The gap is closed by pulling the valuable feedback generated by SIEM, UEBA and SOAR back into the “identify” and “protect” functions. These insights reveal how to better identify risks and protect against them in the future, to (hopefully) prevent the next incident. By closing this gap, security teams can begin to get insights into areas of repeated risk such as:
- Are you responding to the same type of incidents constantly? You might need to shore up your ability to identify that attack-type earlier.
- Is a specific individual or group of individuals causing a disproportionate amount of recovery from your SOC team? They may need additional security controls to protect against their actions.
Elevate Security Platform is a solution that closes this gap. We make your SIEM, UEBA or SOAR better.
The Platform first ingests data from SIEM, UEBA and SOAR solutions, but then combines it with other data from “identify” and “protect” systems (such as user identity, access level, historical actions, attack frequency) to deliver a fuller picture of users most likely to introduce incidents. We eliminate any information silos that may exist between the Incident Response team, GRC personnel, and Security Engineers. By identifying high- and low-risk users and assigning unique security scores, we help apply an understanding of organizational risk that improves your technologies for protection, detection, response and recovery.
To explain how we do this, let’s drill down deeper into one of the three: UEBA solutions.
Elevate Security v. UEBA
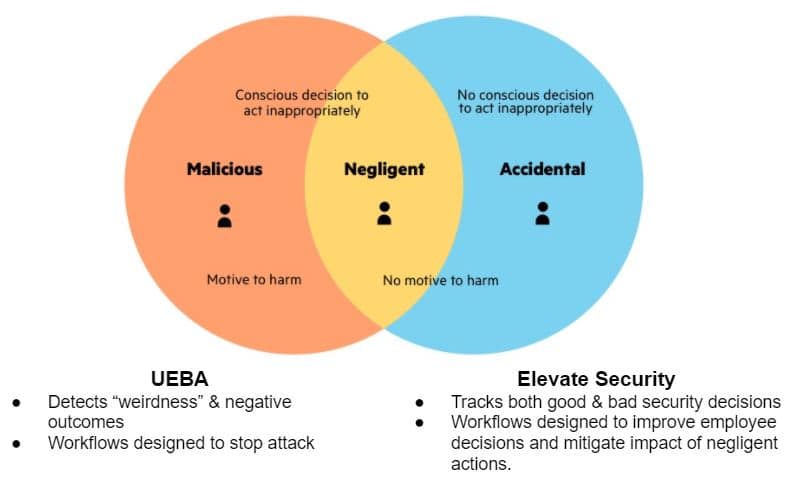
First let’s review how UEBA and Elevate Security Platform are similar. Both pull data from SIEMs, identity solutions and other tools. Both score individual users for benchmarking visibility into your highest risk end users in your workforce.
The main difference between a UEBA solution such as Exabeam and our Platform is that UEBA focuses on finding/fixing the malicious action (such as insider threats), while Elevate focuses on finding/fixing the unintentional action (such as human error).
The problem is that most incident detection & response technologies are still primarily reactive. Even with decades of effort, these solutions alone cannot effectively protect your organization against ransomware, account takeover and data loss. They lack the right context and visibility into these risks.
By incorporating Elevate’s data insights and built-in playbooks, your security team can proactively predict and protect against who might in all likelihood cause the next security incident. Because the majority of the incidents are caused by unintentional insiders, this unique visibility allows security teams to work with the workforce to reduce the likelihood of a successful attack. Future response and recovery then become more adaptive, automated and tailored to those specific threats.
Don’t get us wrong. UEBAs are valuable and Elevate complements these solutions. Together, we better prevent unintentional as well as malicious actions that place your organization at risk. Elevate’s solution then goes the extra mile by enforcing accountability with problem users, providing feedback and active benchmarking of risk over time, further reducing friction in the business.
Where Elevate Security Fits
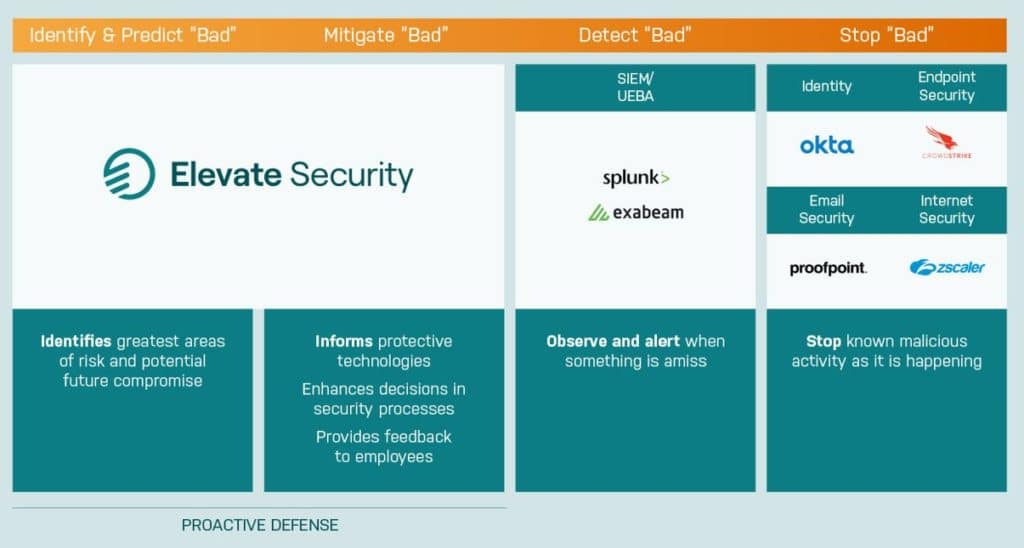
If “bad actions” are the focus, Elevate Security fits neatly into the first 2 buckets of the NIST Cybersecurity Framework: Identify and Protect. Our goal being to “shift left” of loss and not simply detect badness like SIEM, UEBA or SOAR. We help predict risk, prevent incidents, and protect your business before it’s impacted.
If your enterprise already employs one of these three solutions for incident response, consider how a proactive defense technology like Elevate Security Platform can complement and extend your ability to predict (and maybe even prevent) your next cyberattack.










