Predict and Prevent
Data Loss

Problem
It’s no secret that data loss is a huge problem, whether by insider or external threat, malicious or accidental. Intellectual property and customer PII are the two most targeted records. What’s worse, it’s taking organizations an average of 200+ days to detect and identify lost data, and costing them more than $8M to recover from a single breach incident.
External attackers will generally follow similar tactics used in other social engineering schemes to establish an internal foothold. Once established, they can pivot using their victim’s identity to identify and exfiltrate their booty. Insider threats already have privileged access to the organization’s systems. They simply execute data identification and exfiltration in as stealth of a manner as possible, or make a costly mistake.
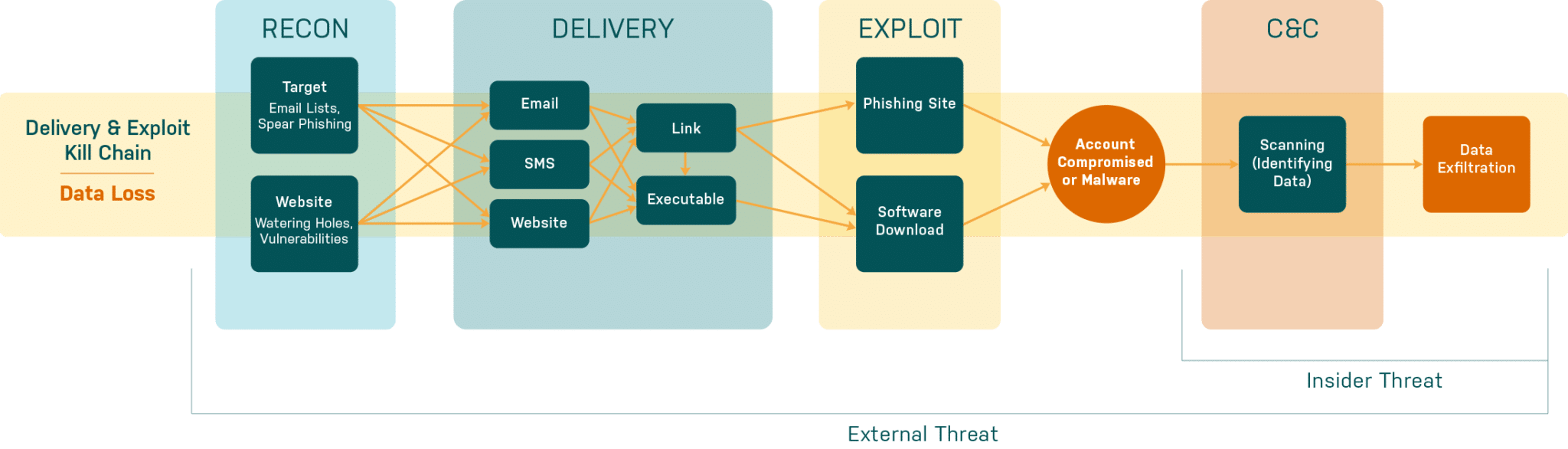
Solution
Elevate Security Platform supports Data Loss Protection with 5 key functions:
Visibility
We build individual risk profiles of every user in your extended enterprise and their likelihood of being targeted for a data theft attack.
Employee Feedback & Executive Communication
Automated notifications inform your riskiest, targeted users about how to correctly protect confidential or sensitive data. We warn them to be on the lookout for malware or phishing attacks so they stay on their toes.
Control Orchestration
We automate the workflow of creating risk-appropriate profiles for targeted individuals. Controls can be tightened or loosened by Elevate pushing updates to DLP, gateways or IAM tools as needed.
Decision Support
The Incident Response team, Helpdesk, and security analysts receive insights into human risk to make educated and defensible decisions.
Continuous Improvement
You can re-evaluate your data loss posture continuously, tracking the effectiveness of your tool and technology investments.
Benefit / Impact
The Elevate Security Platform delivers visibility and control over your attack surface using data you already collect to shine a light on your biggest risks. The security team understands who in your organization is most likely to fall for a ransomware attack. We help you to disrupt the likelihood of IP / data loss, keep all necessary controls up to date automatically, and actively manage your security posture over time. You can protect your risky, targeted employees... while relaxing restrictions around the rest.






