
Users are the most targeted and least protected link in your security program. Employees and contractors can engage in many risky actions online, which can unintentionally lead to cybersecurity attacks on your organization. Luckily, the likelihood of experiencing one of these actions can be measured by monitoring user risk on an individual, departmental, and organizational level.
Much like a credit score predicts your likelihood of paying back a debt, user risk predicts your likelihood of creating a security incident. Similar to a credit score, it's based on your past actions and many other characteristics. Credit risk can be impacted by the amount of outstanding debt, length of debt, and even education and job status. In the case of user risk, characteristics such as the breadth of your access to data and applications, and the likelihood you will be the target of attacks, can affect your score.
With the right user risk mitigation technology, security teams can identify who in an organization is most likely to create a security incident. A user risk profile allows security teams to individually assess the user risk to the organization, pinpointing which users are least and most likely to trigger a security event. With heightened visibility into the online actions of your employees, your organization can become better equipped to mitigate user risk and lower the risk of human-initiated cybersecurity threats as a result.
What can a user risk profile tell you about your employees, and how can your organization benefit from these insights? Let’s dig in.
What is a User Risk Profile?
A user risk profile depicts how likely a person is to take a dangerous action, whether knowingly or unknowingly, that can result in successful phishing, ransomware, malware, or other exploits. Leveraging user risk profiles, security teams will gain insight into employee risk to tailor security controls by individuals, safeguarding risky employees, and even limiting their access to sensitive data. By pinpointing the user risk in your organization, you can prevent cyberattacks before they even begin.
Let’s take a look at two examples of a user risk profile: One is a low-risk user, named Josie, and the second is a high-risk user, named Steven.
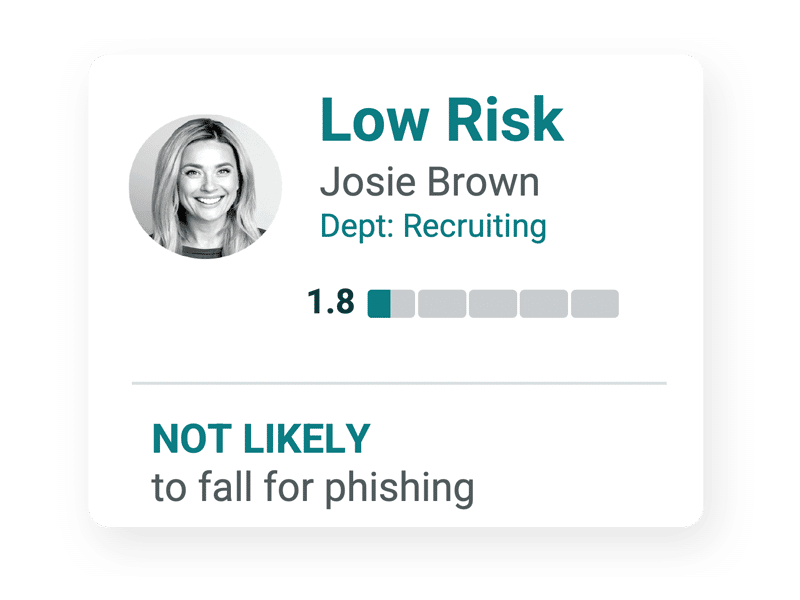
Josie not only detected, but reported all phishing emails she received, and was noted to be “much more likely to report than the rest of the department.” A user risk profile features a user risk score for each employee, which essentially sums up and “grades” their cybersecurity performance. With a strong user risk score, we can infer that Josie is more unlikely to engage in risky activities that could potentially compromise her or the company's data. In fact, Josie will more likely report these cases rather than fall for them.
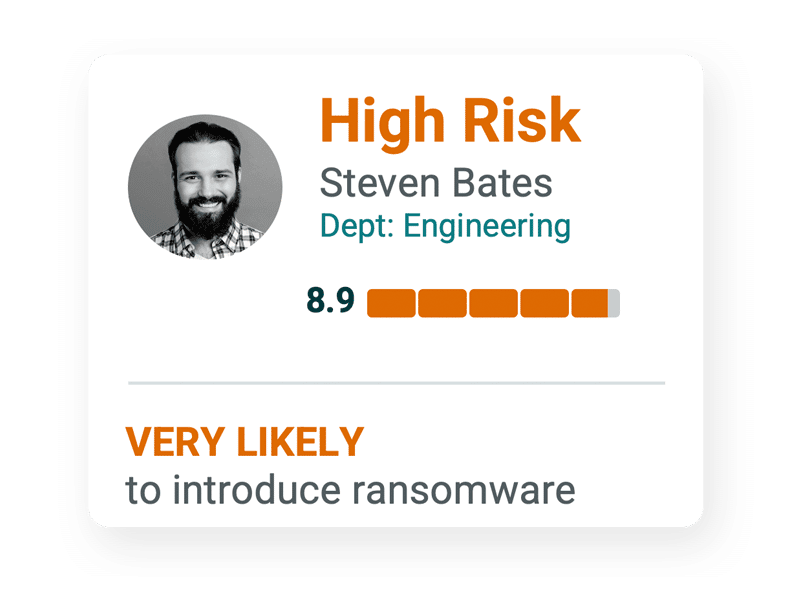
Steven, on the other hand, is a high risk user. Unlike Josie, who detected and reported each phishing email she was sent, Steven did not detect two out of the three, and even failed to report one entirely. While his user risk profile indicates Steven is less likely to fall for a phishing scheme than the rest of his department, it also notes that while his department reported 100% of fraudulent links, he reported none.
Not only do user risk profiles take actions into account, they also take a closer look at the level of access and attackability an individual possesses. For example, Steven may be frequently exposed to data breaches on a regular basis whereas Josie is hardly ever attacked. Statistically, Steven is more likely to fall victim to an attack, simply because they happen to him more frequently. Knowing this, Steven and his company can be more diligent in avoiding attack attempts against him.
In addition to attackability, user risk profiles also examine a user’s access level. Does a high-risk user have access to sensitive company information and data? Do they have the passwords to important business accounts that might be stolen during a security breach? Understanding the potential ‘blast radius’ of each individual helps define the impact and thus the organizational risk that each user represents.
User risk profiles analyze the actions, accessibility, and attackability of each user and enable security teams to:
- Clearly benchmark their higher-risk individuals and departments
- Share real-time and personalized feedback to users, managers, and executives
- Automate business workflows such as case management
- Tailor security controls appropriate to each individual’s risk
With user risk profiles, like Josie and Steven’s, your organization can better understand individual user risk, and compare it to the rest of the department or organization as a whole. Adjustments can be made to high-risk accounts, such as increasing security controls, to limit access to confidential data and mitigate other potential risks. Medium and Low-risk accounts, however, need not be as strongly affected by these controls, optimizing organization productivity. All in all, these profiles provide important insights into employee risk, allowing you to tighten controls around users like Steven without affecting the productivity of responsible users like Josie.
Final Thoughts
When 20% of security breaches involve human error, it’s not at all surprising that organizations spanning all industries are looking for solutions to mitigate user risk. A user risk profile allows organizations to view employee risk at different scales, whether it be individual, departmental, or organizational. This allows your company to proactively identify and mitigate risky user actions, access levels, and attackability — as well as stop cyberattacks in their tracks — by safeguarding high-risk users without hurting productivity in the process.
Learn how to proactively protect your organization from user risk by viewing the Elevate Security Solution Overview.









